In the digital age, smartphones have become integral to our lives. From shopping to carrying out professional tasks, these devices store vast amounts of personal information. Unfortunately, the risk of phone hacking has also increased.
As a result, it poses threats to our privacy and security. So, what are the signs that your phone has been hacked? What methods do hackers use to access your phone? And what steps should you take after a security breach? This comprehensive guide explores what to do when your phone gets hacked.
5 Signs Your Phone Has Been Hacked
Firstly, you need to know the signs indicating someone has hacked your phone. Understanding the signs of a potential phone hack is crucial for timely intervention. Knowing about these can help you take swift action to get control of your phone and personal information.
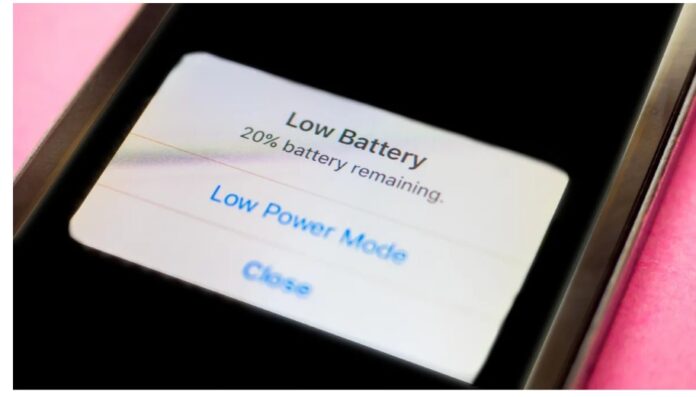
1. Unusual Battery Drain
A sudden and excessive battery drain indicates that someone has illegitimate access and control of your phone. Hacked phones often experience increased power consumption due to malicious processes running in the background. As a result, it can cause the battery to die out quickly.
2. Slow Performance
Sluggish performance and delayed responsiveness are also signs of a phone hack. Hacked devices may suffer from decreased processing speed as malicious software and processes consume system resources. If your phone suddenly becomes slow and unresponsive, you should find the reason.
3. Overheating
Is your phone getting hot even if you are not using it? If yes, it means malicious software might be causing it to overheat. Excessive heat during extraordinary usage is common. But, if your phone becomes unusually hot, it may indicate unauthorized activities.
4. Unexpected Pop-Ups
Intrusive pop-ups or ads on your phone screen indicate someone has hacked your phone. Adware or malware infections can manifest as unwanted pop-ups on your phone. So, it is an alarming sign you need to heed.
5. Unfamiliar Apps or Icons
Hackers may install malicious apps on your device without your knowledge. Therefore, new apps or unfamiliar icons on your home screen clearly indicate potential compromise.
Ways Your Phone Can Be Hacked
There are different ways through which hackers and scammers might try to access your phone. These bad players might use a combination of social engineering techniques and technical trickery to trap people. Some common ways through which a hacker can hack your phone include:
Phishing Attacks
Phishing is a prevalent technique where attackers pose as legitimate entities to trick individuals into providing passwords, credit card details, etc.
The hackers will use deceptive messages, links, or messages to trick people into giving up their sensitive information. Moreover, users may unknowingly click on malicious links, compromising their phone’s security.
Malicious Apps
Downloading infected apps from unofficial sources or malicious app stores can also be the reason behind your phone hack. Users who download apps from unverified sources risk installing malware-infected applications.
These malicious apps can take advantage of the loopholes in the device’s security. They can grant unauthorized access to sensitive data or compromise the overall integrity of the phone.
Public Wi-Fi Vulnerabilities
Hackers can easily break in through your device if your device is connected to unsecured public Wi-Fi networks. Connecting to unsecured public Wi-Fi networks exposes devices to potential hacking attempts.
Hackers can intercept data transmitted over these networks, gaining unauthorized access to sensitive information. This way, they can exploit the potential vulnerabilities in the public Wi-Fi and access your phone.
SIM Card Swapping
Hackers may trick mobile carriers into issuing a new SIM card under their control. With control of the phone number, they can access two-factor authentication codes.
It will allow them to gain unauthorized access to accounts. The primary purpose of a SIM card swap attack is to access your bank accounts via 2FA (2-factor authentication).
Bluetooth Exploits
By exploiting Bluetooth vulnerabilities, hackers can also access and hack your phone. Bluetooth-enabled devices can be vulnerable to attacks if not properly secured. Hackers can exploit Bluetooth weaknesses to gain unauthorized access to a device, potentially compromising sensitive data.
What to Do After Someone Hacks Your Phone?
Finding out your phone has been hacked can be an alarming and distressing experience. However, it’s essential to stay calm and take the relevant action to minimize potential damage and regain control of your device. Here are the steps that you can take after someone hacks your phone.
- Run Antivirus Software – Firstly, thoroughly scan your device using reputable antivirus or anti-malware software. It helps identify and remove any malicious software that might have been installed during the hack.
- Notify Contacts – Another immediate action after your phone has been hacked is to inform your contacts about the security breach. It will help prevent the spread of any malicious activities.
- Update Software – Ensure your phone’s OS (operating system) and other apps have updated security patches. Keeping your software current helps close potential vulnerabilities exploited by hackers.
- Remove Unauthorized Apps – Finding and uninstalling any unfamiliar or suspicious apps from your device is important. Hackers often use malicious apps to maintain control over compromised phones.
- Contact Your Service Provider – Notifying your mobile carrier about the hack. They can assist with securing your account, such as reissuing a new SIM card to prevent SIM swapping attacks.
- Enable Two-Factor Authentication (2FA) – If already not enabled, then activate two-factor authentication on all applicable accounts. It provides an additional security layer by making a secondary verification step necessary, for example, a code sent to your phone.
- Check Account Activity – Review the recent activity on your email, social media, and other accounts for unauthorized actions. Look for unfamiliar logins, password changes, or suspicious transactions.
Responding to a phone hack requires immediate action to contain the breach. It also requires ongoing preventive measures to secure your device and accounts. So, you must take the steps mentioned above to ensure you retain control of your phone after someone hacks it.
What To After Your Phone Has Been Hacked: Recap
On that note, we conclude this article and hope you know what to do if your phone has been hacked. Mobile phones are essential to our social and personal lives, so keeping them safe is highly important. Therefore, you should look for signs showing your phone is hacked and take immediate action.